HOW I NEARLY GOT HACKED VIA LINKEDIN MESSENGER BY MY NEW FRIEND
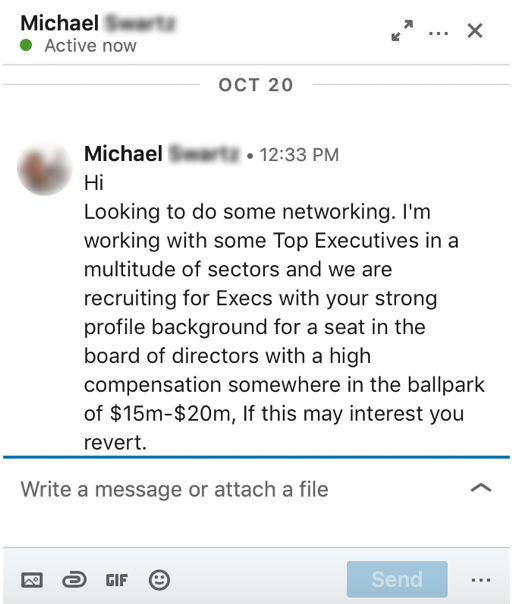
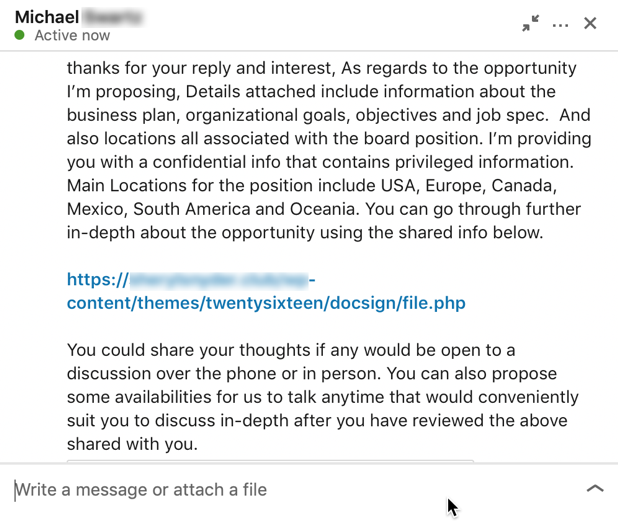
On October 25th, I was contacted via LinkedIn Messenger by a new connection I had added five days earlier. The message was pertaining to a potential business opportunity.
By reading the text and looking at the compensation offered to sit on a board of directors, I had already noticed something wrong; the compensation didn’t make sense. For reasons you will see below, I thought it might just be a mistake, and the person meant to write 20k as opposed to 20M, which would make more sense :)Nonetheless, I wanted to know more. As an entrepreneur, I am always interested in learning about networking opportunities, like this one.
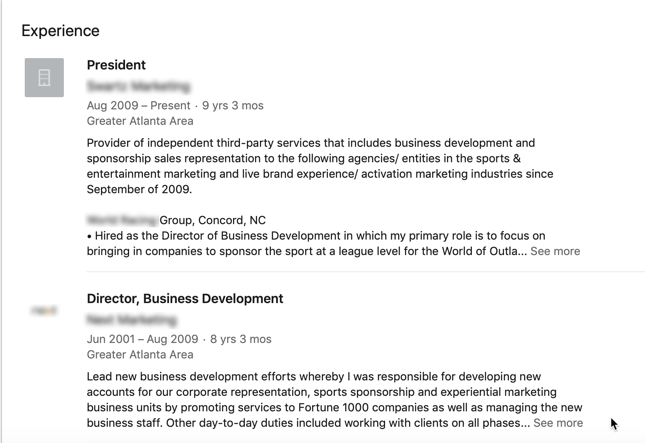
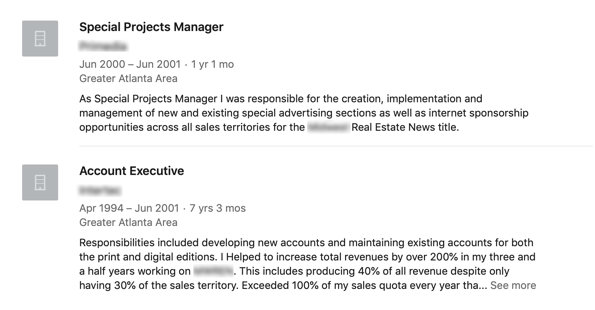
At first sight, I saw nothing alarming about the profile. My new ‘’LinkedIn friend’’ had over 500 connections, and his professional description was looking pretty good.The profile also showed a very credible career path with multiple job experiences over a long period of time.
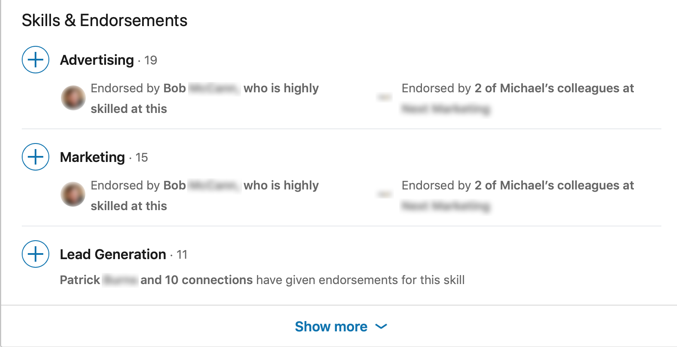
Looking deeper into the profile, I also saw that this person was endorsed by multiple LinkedIn users—some of whom were also highly skilled and highly endorsed. Everything seemed to be legit with the profile in question.
One thing I always like to do is read people’s recommendations before I engage with a new connection. My new ‘’ LinkedIn friend’’ had over 10 recommendations, and that’s more than acceptable for most LinkedIn users. The recommendations he received also seemed to be legit.
At this point—and after verifying all the basics of this profile—I decided to engage in the conversation and see how that would go. A few seconds later, I received a new message from this person with a brief description of the opportunity and a link to access the information.
After reading his message and looking at the nature of the link, I already knew what was going on.
Let’s start by the message itself:
- The person is proposing to share some confidential and sensitive information with me, such as: a business plan, organizational goals, key objectives, and more without asking for a non-disclosure agreement (NDA) to be signed or even a phone call.
Now, let’s look at the link:
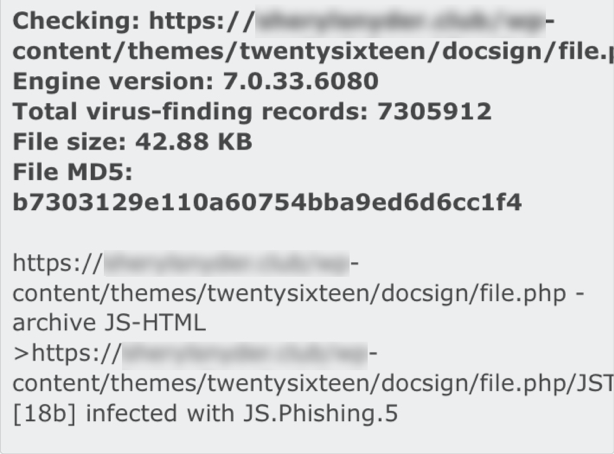
That link looks phishy!
“Why would someone share a PHP file from within a theme’s directory!?” said one of our security consultants at Orenda Security.
When a WordPress site is compromised, the theme’s directory is usually one of the easiest aspects to modify, so you can incorporate your own PHP code.
This type of link is uncommon for exchanging this type of electronic document or information, especially for a known company, like DocuSign.
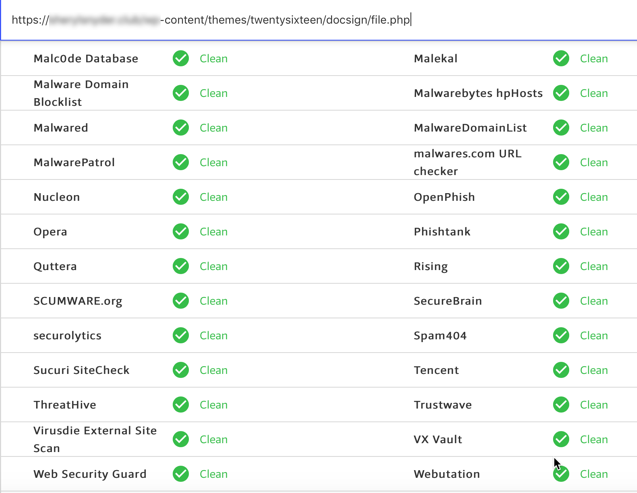
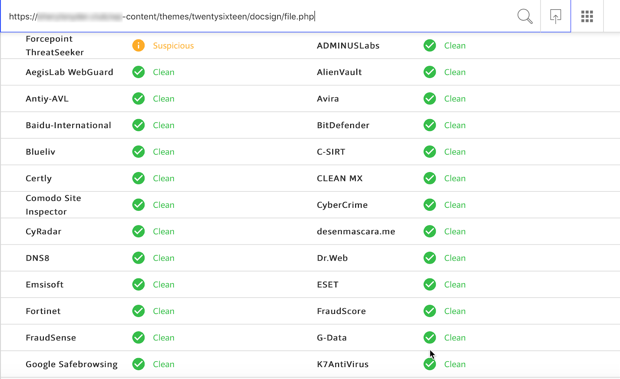
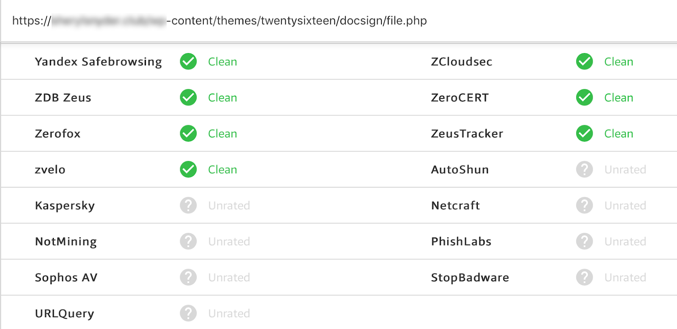
Using a free, top-ranked Google website, I scanned the URL for malicious activity. The resultswere surprising, and full of green. If you’ve never used a website like this one before, just know that there are hundreds of them that offer free scanning services. This site utilizes multiple scanning sites and only one indicated that something was suspicious.
I guess it’s fair to say that some people would trust the link based on the scan results.
Just for fun, I tested the link on Mac, and the antivirus (a trusted one) did not pick it up either.
Unfortunately, without proper guidance from a trusted expert or without having completed a security awareness course, it’s safe to say that a click could be the next step for many users.
In fact, the link is delivering a JS.Phishing.5 spear phishing attack:
Now, let’s see what this cybercriminal had in mind.
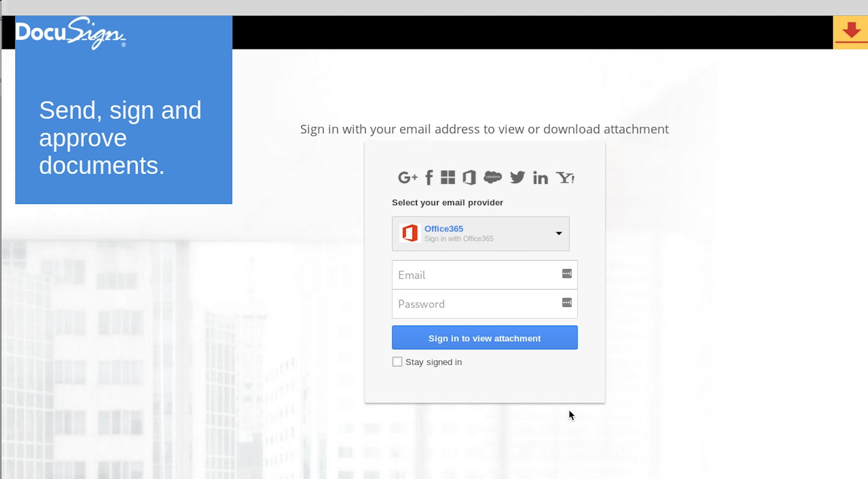
When opening the link in a secured environment, a fake DocuSign login portal was displayed, requesting me to login with either Office 365, Gmail, Facebook, or other known providers.
On first glance, the page itself is not bad. A lot of people could fall for the scam and I’m sure many already have.
Characteristics of this phishing scenario:
- The overall look is of poor quality and does not reflect the corporate image of a serious organization. ·
- There are no spelling or grammatical errors, which used to be one of the most common indicators of a fake landing page. However, phishing attacks are getting more and more sophisticated, and of course you cannot rely solely on this aspect.
- The logo and the branding don’t correspond to the real DocuSign format.
- None of the links on the page are functional.
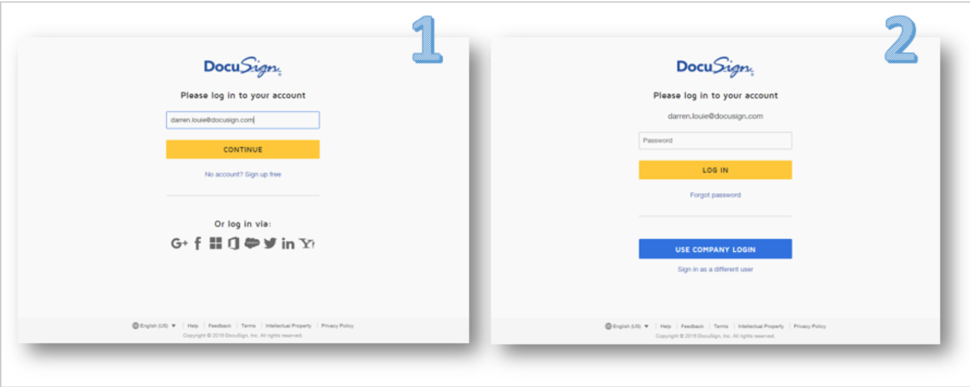
If you go directly on the official DocuSign website, it’s easy to see what the real login page should be. Even a simple Google search will guide you.
Real DocuSign login pages (from support.docusign.com):
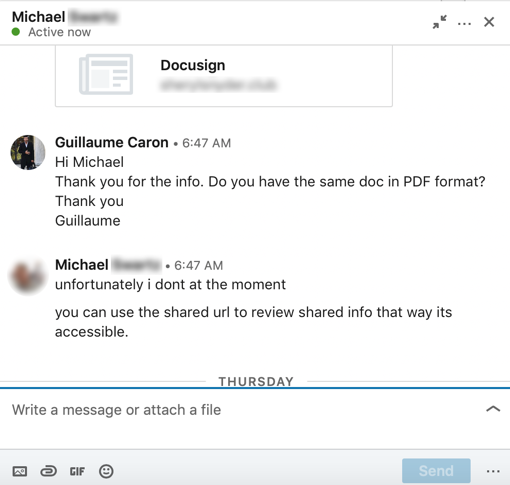
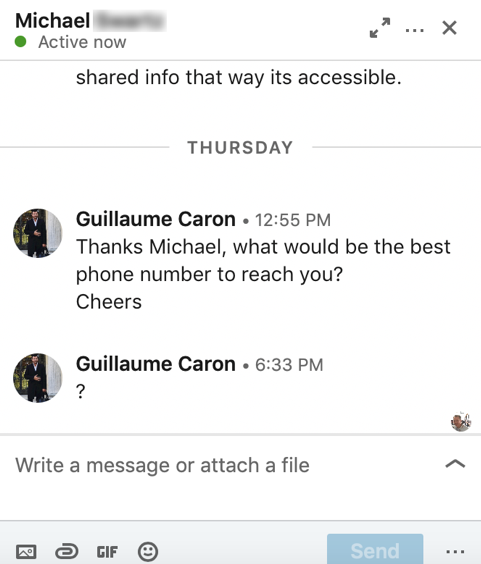
The next morning, I wanted to know more about this hacker, so I asked my new friend if they had a PDF document instead because I wanted to keep the conversation going a little longer.
Below was their answer:
I also asked them for a good phone number to discuss this “opportunity”.
But, of course, I did not get a response from the person.
At this point—and for obvious reasons—it was important to report this account to LinkedIn, so they could protect other LinkedIn members. We have also hid the name of the profile user in this post because it is very possible that this account was compromised and is now controlled by a malicious user without the real account owner knowing it. I also noticed that we had two connections in common and made sure they knew about this situation, so they wouldn’t get phished. Although, they could also be working together…
The reason why I’ve taken the time to share this experience with you is to show you that, when it comes to phishing attacks, most people think that it only happens via personalized or generic emails. However, hackers use all kinds of methods to target their victims, such as social media, text messaging (#smishing), and even LinkedIn Messenger.
I have the chance to work every day with a group of elite cybersecurity experts at Orenda Security. I also had the chance to work in the cybersecurity awareness business for a decade, helping organizations of all sizes with security awareness programs and phishing simulations services. However, that is not the case for most professionals outside of the cybersecurity world, and this direct attack via LinkedIn Messenger can be devastating for any of us.
Just remember to stay alert at all times, and if you have any doubts or find yourself in a similar situation, just reach out to someone that can help you. You can also ignore the message, but don’t open any links. If it’s a real opportunity or something important, that person will find a better way to reach out to you anyway!